From: nick@npdoty.name
Date: 1/01/2019 01:30:00 PM Bcc: https://bcc.npdoty.name/
We've spent a lot of collective time and effort on design and policy to support the privacy of the user of a piece of software, whether it's the Web or a mobile app or a device. But more current and more challenging is the privacy of the non-user of the app, the privacy of the bystander. With the ubiquity of sensors, we are increasingly observed, not just by giant corporations or government agencies, but by, as they say, little brothers.
Consider the smartphone camera. Taking digital photos is free, quick and easy; resolution and quality increase; metadata (like precise geolocation) is attached; sharing those photos is easy via online services. As facial recognition has improved, it has become easier to automatically identify the people depicted in a photo, whether they're the subject of a portrait or just in the background. If you don't want to share records of your precise geolocation and what you're doing in public places, with friends, family, strangers and law enforcement, it's no longer enough to be careful with the technology you choose to use, you'd also have to be constantly vigilant about the technology that everyone around you is using.
While it may be tempting to draw a "throw your hands up" conclusion from this -- privacy is dead, get over it, there's nothing we can easily do about it -- we actually have widespread experience with this kind of value and various norms to protect it. At conferences and public events, it's not uncommon to have a system of stickers on nametags to either opt-in or opt-out of photos. This is a help (not a hindrance) for event photographers: rather than asking everyone to pose in your photo, or asking everyone after the fact if they're alright with your posting a public photo, or being afraid of posting a photo and facing the anger of your attendees, you can just keep an eye on the red and green dots on those plastic nametags and feel confident that you're respecting the attendees at your event.
There are similar norms in other settings. Taking video in the movie theater violates legal protections, but there are also widespread and reasonably well-enforced norms against capturing video of live theater productions or comedians who test out new material in clubs, on grounds that may not be copyright. Art museums will often tell you whether photos are welcome or prohibited. In some settings the privacy of the people present is so essential that unwritten or written rules prohibit cameras altogether: at nude hot springs, for example, you just can't use a camera at all. You wouldn't take a photo in the waiting room of your doctor's office and you'll invite anger and social confrontation if you're taking photos of other people's children at your local playground.
And even in "public" or in contexts with friends, there are spoken or unspoken expectations. "Don't post that photo of me drinking, please." "Let me see how I look in that before you post it on Facebook." "Everyone knows that John doesn't like to have his photo taken."
As cameras become small and more widely used, and encompass depictions of more people, and are shared more widely and easily, and identifications of depicted people can also be shared, our social norms and spoken discussions don't easily keep up. Checking with people before you post a photo of them is absolutely a good practice and I encourage you to follow it. But why not also use technology to facilitate this checking others' preferences?
We have all the tools we need to make "no photos please" nametag stickers into unobtrusive and efficiently communicated messages. If you're attending a conference or party and don't want people to take your photo, just tap the "no photos please" setting on your smartphone before you walk in. And if you're taking photos at an event, your camera will show a warning when it knows that someone in the room doesn't want their photo taken, so that you can doublecheck with the people in your photo and make sure you're not inadvertently capturing someone in the background. And the venue can remind you that way too, in case you don't know the local norm that pictures shouldn't be taken in the church or museum.
As a technical matter, I think we're looking at Bluetooth broadcast beacons, from smartphones or stationary devices. That could be a small Arduino-based widget on the wall of a commercial venue, or one day you might have a poker-chip-sized device in your pocket that you can click into private mode. When you're using a compatible camera app on your phone or a compatible handheld camera, your device regularly scans for nearby Bluetooth beacons and if it sees a "no photos please" message, it shows a (dismissable) warning.

The discretionary communication of preferences is ideal in part because it isn't self-enforcing. For example, if the police show up at the political protest you're attending and broadcast a "no photos please" beacon, you can (and should) override your camera warning to take photos of their official activity, as a safeguard for public safety and accountability. An automatically-enforcing DRM-style system would be both infeasible to construct and, if it were constructed, inappropriately inviting to government censorship or aggressive copyright maximalism. Technological hints are also less likely to confusingly over-promise a protection: we can explain to people that the "no photos please" beacon doesn't prevent impolite or malicious people from surreptitiously taking your photo, just as people are extremely familiar with the fact that placards, polite requests and even laws are sometimes ignored.
Making preferences technically available could also help with legal compliance. If you're taking a photo at an event and get a "no photos" warning, your device UI can help you log why you might be taking the photo anyway. Tap "I got consent" and your camera can embed metadata in the file that you gathered consent from the depicted people. Tap "Important public purpose" at the protest and you'll have a machine-readable affirmation in place of what you're doing, and your Internet-connected phone can also use that signal to make sure photos in this area are promptly backed up securely in case your device is confiscated.
People's preferences are of course more complicated than just "no photos please" or "sure, take my photo". While I, like many, have imagined that sticky policies could facilitate rules of how data is subsequently shared and used, there are good reasons to start with the simple capture-time question. For one, it's familiar, from these existing social and legal norms. For another, it can be a prompt for real-time in-person conversation. Rather than assuming an error-free technical-only system of preference satisfaction, this can be a quick reminder to check with the people right there in front of you for those nuances, and to do so prior to making a digital record.
Broadcast messages provide opportunities that I think we haven't fully explored or embraced in the age of the Internet and the (rightfully lauded) end-to-end principle. Some communications just naturally take the form of letting people in a geographic area know something relevant to the place. "The cafe is closing soon." "What's the history of that statue?" "What's the next stop on this train and when are we scheduled to arrive?" If WiFi routers included latitude and longitude in the WiFi network advertisement, your laptop could quickly and precisely geolocate even in areas where you don't have Internet access, and do so passively, without broadcasting your location to a geolocation provider. (That one is a little subtle; we wrote a paper on it back when we were evaluating the various privacy implications of WiFi geolocation databases at Berkeley.) What about, "Anyone up for a game of chess?" (See also, Grindr.) eBook readers could optionally broadcast the title of the current book to re-create the lovely serendipity of seeing the book cover a stranger is reading on the train. Music players could do the same.
The Internet is amazing for letting us communicate with people around the world around shared interests. We should see the opportunity for networking technology to also facilitate communications, including conversations about privacy, with those nearby.
Some end notes that my head wants to let go of: There is some prior art here that I don't want to dismiss or pass over, I just think we should push it further. A couple examples:
- Google folks have developed broadcast URLs that they call The Physical Web so that real-life places can share a Web page about them (over mDNS or Bluetooth Low Energy) and I hope one day we can get a link to the presenter's current slide using networking rather than everyone taking a picture of a projected URL and awkwardly typing it into our laptops later.
- The Occupy movement showed an interest in geographically-located Web services, including forums and chatrooms that operate over WiFi but not connected to the Internet. Occupy Here:
Anyone within range of an Occupy.here wifi router, with a web-capable smartphone or laptop, can join the network “OCCUPY.HERE,” load the locally-hosted website http://occupy.here, and use the message board to connect with other users nearby.
Getting a little further afield but still related, it would be helpful if the network provider could communicate directly with the subscriber using the expressive capability of the Web. Lacking this capability, we've seen frustrating abuses of interception: captive portals redirect and impersonate Web traffic; ISPs insert bandwidth warnings as JavaScript insecurely transplanted into HTTP pages. Why not instead provide a way for the network to push a message to the client, not by pretending to be a server you happen to connect to around that same time, but just as a clearly separate message? ICMP control messages are an existing but underused technology.
Labels: broadcast, wifi, privacy
From: nick@npdoty.name
Date: 1/14/2018 03:58:00 PM To: myself, others in my industry Bcc: https://bcc.npdoty.name/
A reminder:
Unconstrained media access to a person is indistinguishable from harassment.
It pains me to watch my grandfather suffer from surfeit of communication. He can't keep up with the mail he receives each day. Because of his noble impulse to charity and having given money to causes he supports (evangelical churches, military veterans, disadvantaged children), those charities sell his name for use by other charities (I use "charity" very loosely), and he is inundated with requests for money. Very frequently, those requests include a "gift", apparently in order to induce a sense of obligation: a small calendar, a pen and pad of paper, refrigerator magnets, return address labels, a crisp dollar bill. Those monetary ones surprised me at first, but they are common and if some small percentage of people feel an obligation to write a $50 check, then sending out a $1 to each person makes it worth their while (though it must not help the purported charitable cause very much, not a high priority). Many now include a handful of US coins stuck to the response card -- ostensibly to imply that just a few cents a day can make a difference, but, I suspect, to make it harder to recycle the mail directly because it includes metal as well as paper. (I throw these in the recycling anyway.) Some of these solicitations include a warning on the outside that I hadn't seen before, indicating that it's a federal criminal offense to open postal mail or to keep it from the recipient. Perhaps this is a threat to caregivers to discourage them from throwing away this junk mail for their family members; I suspect more likely, it encourages the suspicion in the recipient that someone might try to filter their mail, and that to do so would be unjust, even criminal, that anyone trying to help them by sorting their mail should not be trusted. It disgusts me.
But the mails are nothing compared to the active intrusiveness of other media. Take conservative talk radio, which my grandfather listened to for years as a way to keep sound in the house and fend off loneliness. It's often on in the house at a fairly low volume, but it's ever present, and it washes over the brain. I suspect most people could never genuinely understand Rush Limbaugh's rants, but coherent argument is not the point, it's just the repetition of a claim, not even a claim, just a general impression. For years, my grandfather felt conflicted, as many of his beloved family members (liberal and conservative) worked for the federal government, but he knew, in some quite vague but very deep way, that everyone involved with the federal government was a menace to freedom. He tells me explicitly that if you hear something often enough, you start to think it must be true.
And then there's the TV, now on and blaring 24 hours a day, whether he's asleep or awake. He watches old John Wayne movies or NCIS marathons. Or, more accurately, he watches endless loud commercials, with some snippets of quiet movies or television shows interspersed between them. The commercials repeat endlessly throughout the day and I start to feel confused, stressed and tired within a few hours of arriving at his house. I suspect advertisers on those channels are happy with the return they receive; with no knowledge of the source, he'll tell me that he "really ought to" get or try some product or another for around the house. He can't hear me, or other guests, or family he's talking to on the phone when a commercial is on, because they're so loud.
Compared to those media, email is clear and unintrusive, though its utility is still lost in inundation. Email messages that start with "Fw: FWD: FW: FW FW Fw:" cover most of his inbox; if he clicks on one and scrolls down far enough he can get to the message, a joke about Obama and monkeys, or a cute picture of a kitten. He can sometimes get to the link to photos of the great-grand-children, but after clicking the link he's faced with a moving pop-up box asking him to login, covering the faces of the children. To close that box, he must identify and click on a small "x" in very light grey on a white background. He can use the Web for his bible study and knows it can be used for other purposes, but ubiquitous and intrusive prompts (advertising or otherwise) typically distract him from other tasks.
My grandfather grew up with no experience with media of these kinds, and had no time to develop filters or practices to avoid these intrusions. At his age, it is probably too late to learn a new mindset to throw out mail without a second thought or immediately scroll down a webpage. With a lax regulatory environment and unfamiliar with filtering, he suffers -- financially and emotionally -- from these exploitations on a daily basis. Mail, email, broadcast video, radio and telephone could provide an enormous wealth of benefits for an elderly person living alone: information, entertainment, communication, companionship, edification. But those advantages are made mostly inaccessible.
Younger generations suffer other intrusions of media. Online harassment is widely experienced (its severity varies, by gender among other things); your social media account probably lets you block an account that sends you a threat or other unwelcome message, but it probably doesn't provide mitigations against dogpiling, where a malicious actor encourages their followers to pursue you. Online harassment is important because of the severity and chilling impact on speech, but an analogous problem of over-access exists with other attention-grabbing prompts. What fraction of smartphone users know how to filter the notifications that buzz or ring their phone? Notifications are typically on by default rather than opt-in with permission. Smartphone users can, even without the prompt of the numerous thinkpieces on the topic, describe the negative effects on their attention and well-being.
The capability to filter access to ourselves must be a fundamental principle of online communication: it may be the key privacy concern of our time. Effective tools that allow us to control the information we're exposed to are necessities for freedom from harassment; they are necessities for genuine accessibility of information and free expression. May there be shared blocklists, content warnings, notification silencers, readability modes and so much more.
Labels: mail, harassment, blocklists, accessibility, privacy
From: npdoty@ischool.berkeley.edu
Date: 6/17/2016 05:34:00 PM To: friends from Berkeley and the standards/indieweb world Bcc: https://bcc.npdoty.name/
Friends,
I welcome feedback on an experimental feature, exploring ephemerality and URLs, or “ephemerurls”. Here’s the idea: sometimes I’ve posted something on my website that I want to share with some colleagues, but the thing isn’t quite finished yet. I might want to post the URL in some forum (an IRC or Slack channel, an archived mailing list, or on Twitter), but I don’t want the generally accessible URL to be permanently, publicly archived in one of those settings. That is, I want to give out a URL, but the URL should only work temporarily.
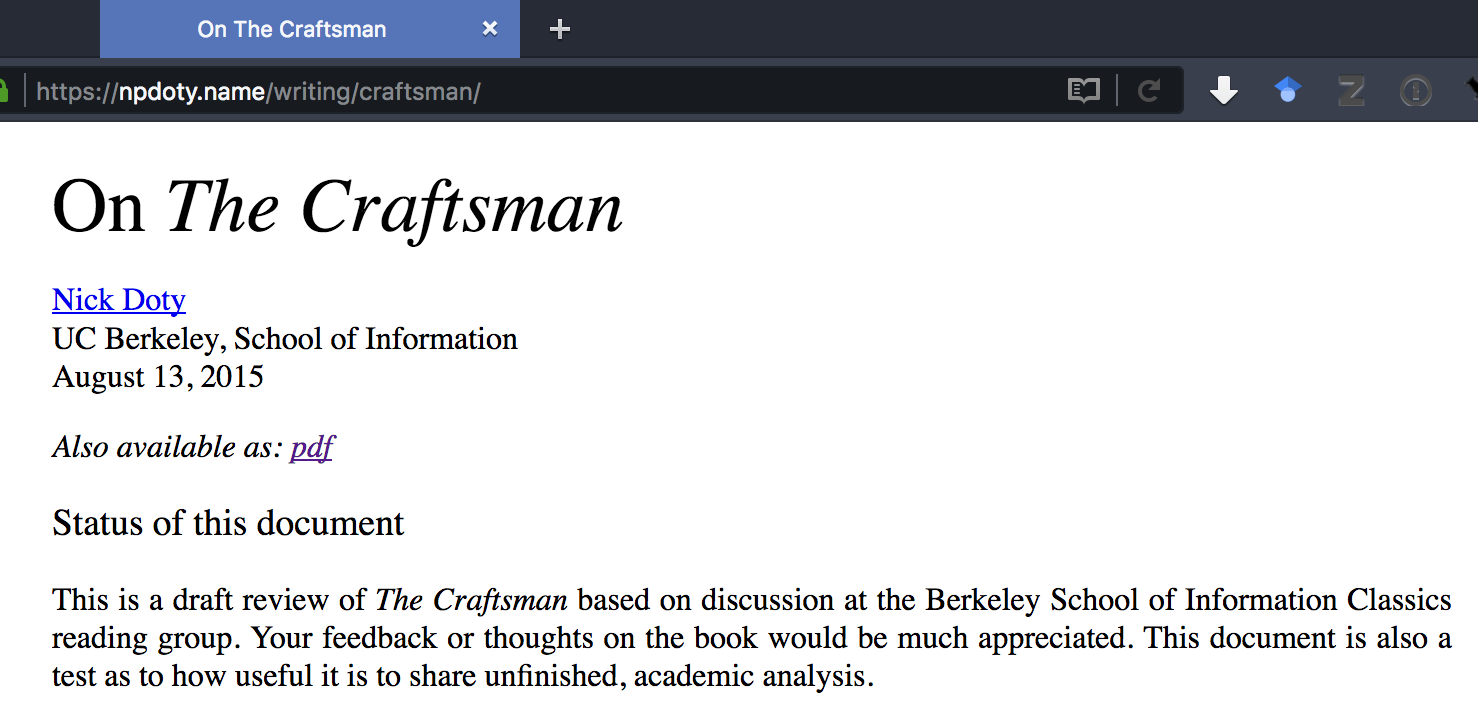
Ephemerurl is a service I’ve built and deployed on my own site. Here’s how it works. Let’s say I’ve been working on a piece of writing, a static HTML page, that I want to share just for a little while for some feedback. Maybe I’m presenting the in-progress work to a group of people at an in-person or virtual meeting and want to share a link in the group’s chatroom. Here’s a screenshot of that page, at its permanent URL:
I decide I want to share a link that will only work until 6pm this afternoon. So I change the URL, and add “/until6pm/” between “npdoty.name” and the rest of the URL. My site responds:
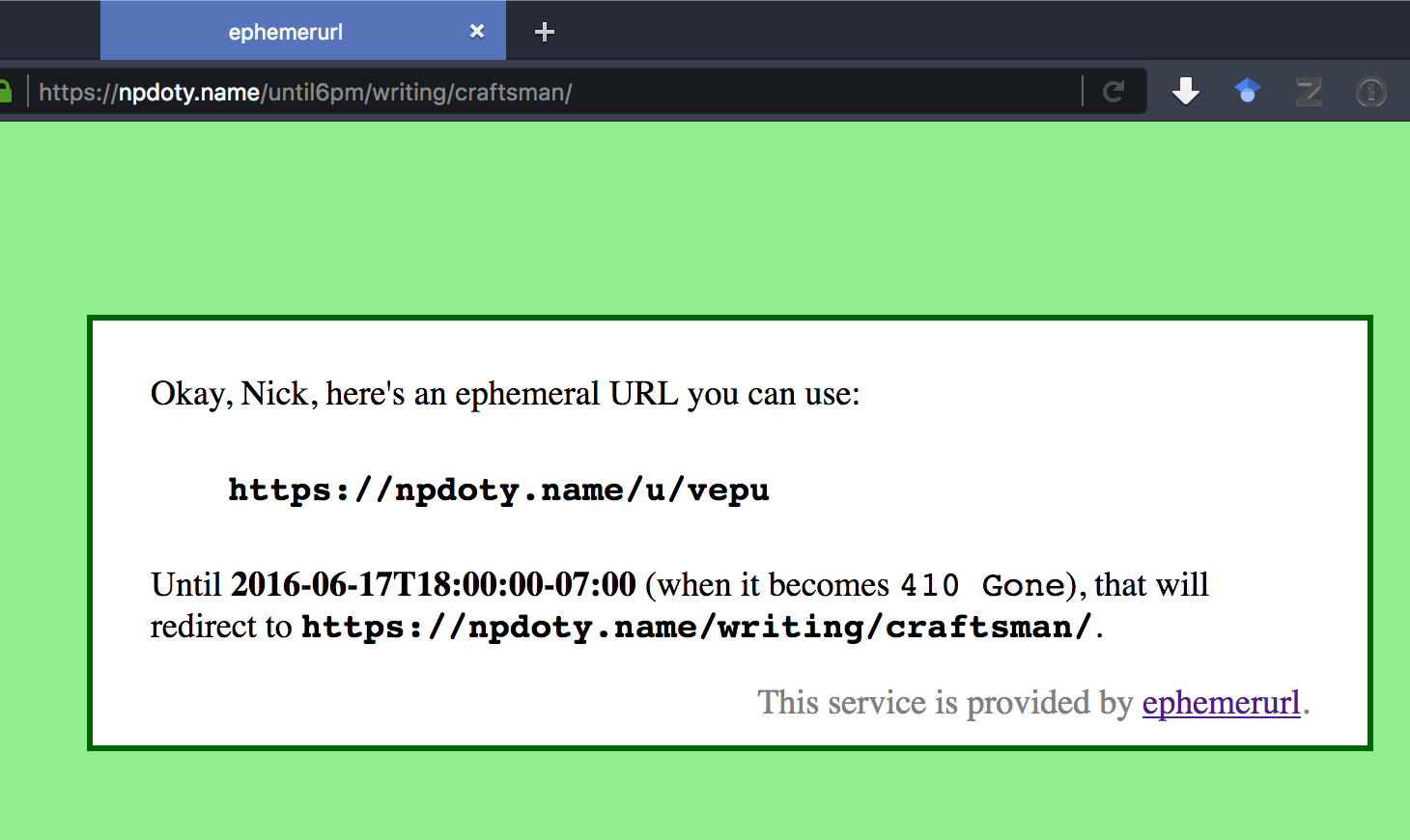
“Okay, Nick, here’s an ephemeral URL you can use” Great, I copy and paste this opaque, short URL into the chatroom: https://npdoty.name/u/vepu
Right now, that URL will redirect to the original page. (But if you don’t see this email until after 6pm my time, you’ll instead get a 410 Gone error message.) But if the chatroom logs are archived after our meeting (which they often are in groups where I work), the permanent link won’t be useful.
Of course, if you follow a URL like that, you might not realize that it’s intended to be a time-boxed URL. So the static page provides a little disclosure to you, letting you know this might not be public, and suggesting that if you share the URL, you use the same ephemeral URL that you received.
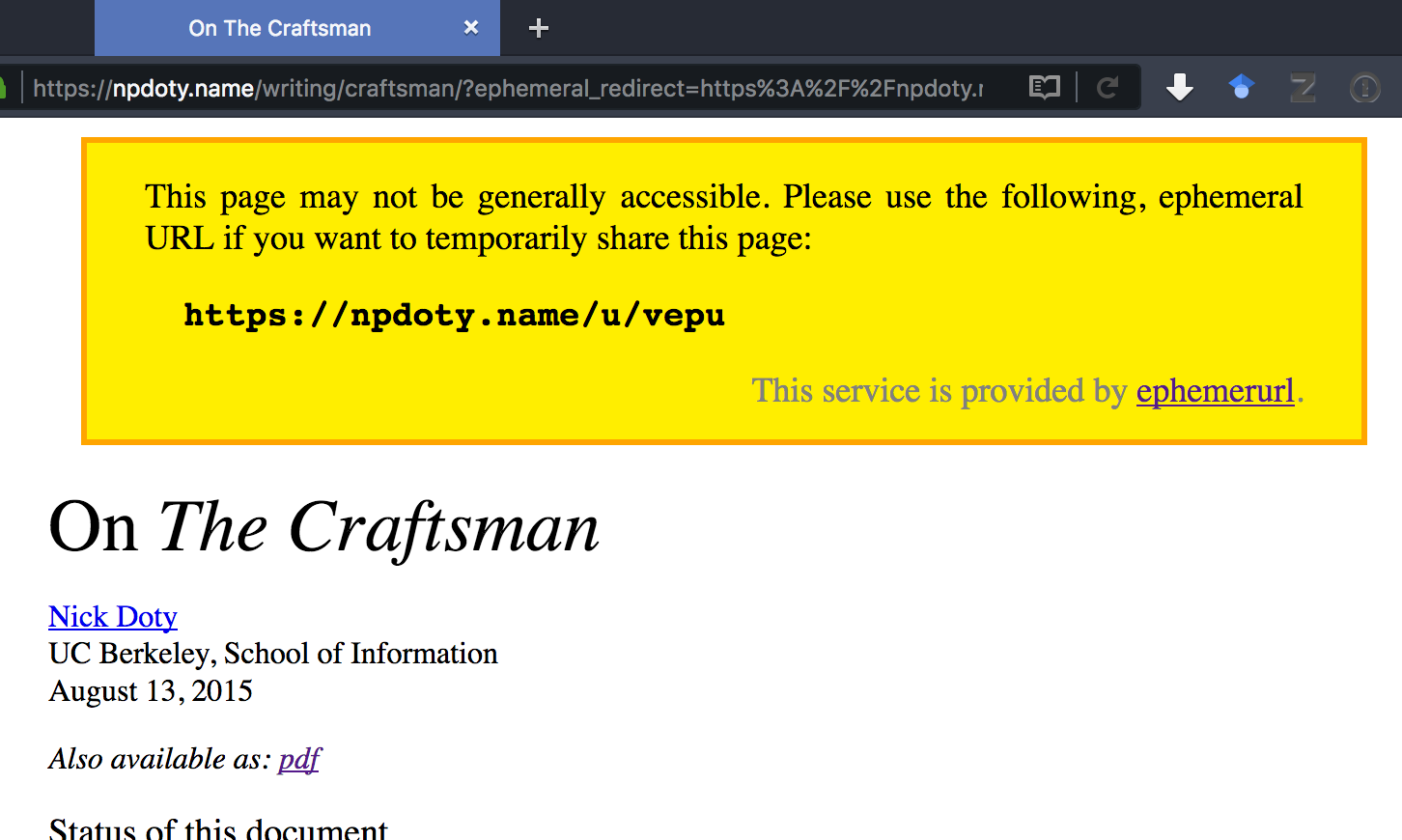
This builds on a well-known pattern. Private, “unguessable” links are a common way of building in a kind of flexible privacy/access-control into our use of the Web. They’re examples of Capability URLs. Sites will often, when accessing a private or capability URL, provide a warning to the user letting them know about the sharing norms that might apply:
But ephemerurls also provide a specific, informal ephemerality, another increasingly popular privacy feature. It’s not effective against a malicious attacker — if I don’t want you to see my content or I don’t trust you to follow some basic norms of sharing, then this feature won’t stop you, and I’m not sure anything on the Web really could — but it uses norms and the way we often share URLs to introduce another layer of control over sharing information. Snapchat is great not because it could somehow prevent a malicious recipient from taking a screenshot, but because it introduces a norm of disappearance, which makes a certain kind of informal sharing easier.
I’d like to see the same kinds of sharing available on the Web. Disappearing URLs might be one piece, but folks are also talking about easy ways to make social media posts have a pre-determined lifetime where they’ll automatically disappear.
What do you think? Code, documentation, issues, etc. on Github.
Update: it’s been pointed out (thanks Seb, Andrew) that while I’ve built and deployed this for my own domain, it would also make sense to have a standalone service (you know, like bit.ly) that created ephemeral URLs that could work for any page on the Web without having to install some PHP. It’s like perma.cc, but the opposite. See issue #1.
Cheers,
Nick
P.S. Thanks to the Homebrew Website Club for their useful feedback when I presented some of this last month.
Labels: Web, ephemerality, privacy
From: nick@npdoty.name
Date: 9/29/2014 05:49:12 PM To: kylewm.com Bcc: https://bcc.npdoty.name/
Hi Kyle,
It's nice to think about for services that are backing-up/syndicating content from social networking sites. And comparing that disclaimer to the current situation is a useful reminder. It's great to be conscious of the potential privacy advantages but just generally the privacy implications of decentralized technologies like the Web.
Is there an etiquette about when it's fine and when it's not to publish a copy of someone's Twitter post? We may develop one, but in the meantime, I think that when someone has specifically replied to your post, it's in context to keep a copy of that post.
Nick
P.S. This is clearly mostly just a test of the webmention-sending code that I've added to this Bcc blog, but I wanted to say bravo anyway, and why not use a test post to say bravo?
Labels: web, webmention, indieweb, privacy
From: nick@npdoty.name
Date: 8/27/2014 10:47:22 PM To: Aaron Parecki Bcc: https://bcc.npdoty.name/
I did make it to the this evening after all, in Portland this time, since I happened to be passing through.
I was able to show off some of the work I've been doing on embedding data-driven graphs/charts in the Web versions of in-progress academic writing: d3.js generating SVG tables in the browser, but also saving SVG/PDF versions which are used as figures in the LaTeX/PDF version (which I still need for sharing the document in print and with most academics). I need to write a brief blog post describing my process for doing this, even though it's not finished. In fact, that's a theme; we all need to be publishing code and writing blog posts, especially for inchoate work.
Also, I've been thinking about pseudonymity in the context of personal websites. Is there anything we need to do to make it possible to maintain different identities / domain names without creating links between them? Also, it may be a real privacy advantage to split the reading and writing on the Web: if you don't have to create a separate list of friends/follows in each site with each pseudonym, then you can't as easily be re-identified by having the same friends. But I want to think carefully about the use case, because while I've become very comfortable with a domain name based on my real name and linking my professional, academic and personal web presences, I find that a lot of my friends are using pseudonyms, or intentionally subdividing
Finally, I learned about some cool projects.
- Indiewebcamp IRC logs become more and more featureful, including an interactive chat client in the logs page itself
- Google Web Starter Kit provides boilerplate and a basic build/task system for building static web sites
- Gulp and Harp are two (more) JavaScript-based tools for preparing/processing/hosting static web sites
All in all, good fun. And then I went to the Powell's bookstore dedicated just to technical and scientific books, saw an old NeXT cube and bought an old book on software patterns.
Thanks for hosting us, @aaronpk!
— Nick
Labels: indiewebcamp, rsvp, portland, privacy